While studying the edX Cyber Security course, I became aware of the prevalence of data breaches and cybersecurity threats, and grew concerned about the indispensable roles that social media platforms like Facebook, TikTok, and Instagram play in daily life.
TikTok, as a prominent video-sharing platform with millions of users, has recently emerged as a focal point of security concerns. My research into zero-click attacks during this course has unveiled both the intriguing complexity and alarming implications of these vulnerabilities. Zero-Click attacks, as discussed in the course, exploit weaknesses in software and systems without requiring any action from the user beyond initial exposure to the malicious payload. This characteristic makes them particularly insidious and challenging to detect.
Understanding Zero-Click Attacks
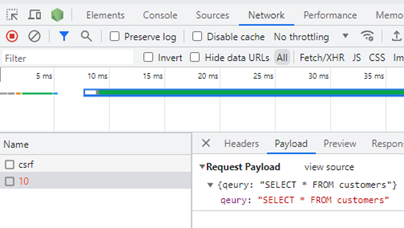
Zero-click attacks pose a significant threat by surreptitiously compromising user data and potentially gaining control over devices. Unlike traditional phishing or social engineering methods that rely on user interaction, zero-click attacks execute automatically upon delivery of the malicious code. This often occurs through vulnerabilities in messaging services, where a carefully crafted message can initiate the attack without the user's awareness.

Mitigating Zero-Click Attacks
To combat zero-click attacks effectively, robust security measures are imperative. Regular software updates, advanced endpoint protection, and intrusion detection systems are essential components of a proactive defence strategy. Additionally, limiting app permissions and engaging ethical hackers to identify vulnerabilities can enhance resilience against such attacks. Educating users about zero-click threats and promoting adherence to secure practices further strengthens overall cybersecurity posture.
Conclusion
In conclusion, the growing complexity of software systems amplifies the potential for zero-click vulnerabilities. Vigilance, proactive security measures, and continuous monitoring are crucial to safeguarding against these silent yet pernicious threats. By implementing these recommendations, organisations and individuals can mitigate the risks posed by zero-click attacks and preserve the integrity of their digital environments.